The undeniable truth is that cyber attacks are inevitable, and no system is absolutely secure. A system that appears protected today might be vulnerable tomorrow.
But what if you had a fully equipped team ready to face these threats? A team that works in perfect coordination, managing tools, processes, and decisions quickly and accurately to effectively repel attacks. What makes this team capable of maintaining your organization's security despite all the risks?
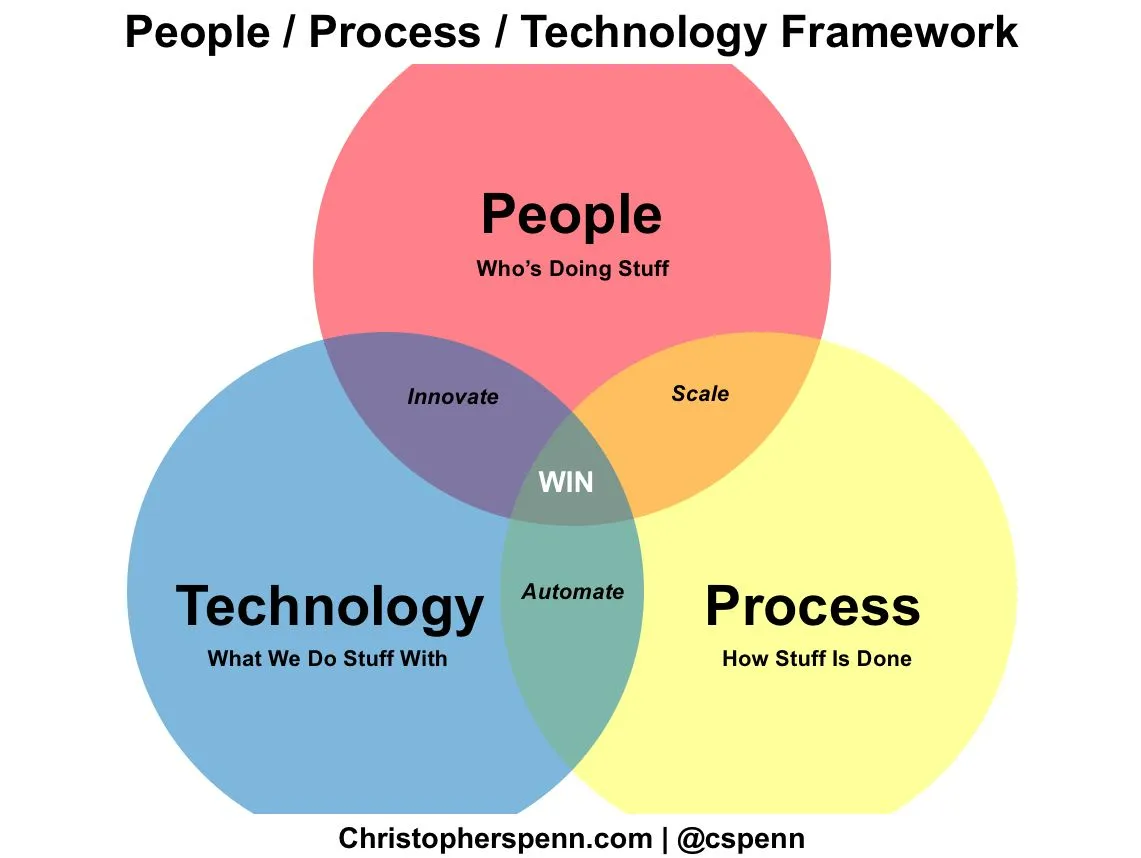
The answer lies in three essential components, which, when properly coordinated, become an effective line of defense protecting you from any threat. What are these components that make your team invincible?
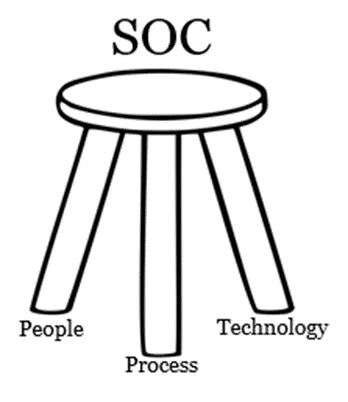
The answer lies in three core components known as the "Success Triad" or People, Process, and Technology. These elements represent a "three-legged stool," and an SOC cannot function or succeed without any one of them.
1. People: The Core Talent
No blue team can succeed without qualified human elements who possess the necessary skills to perform tasks and interact effectively with processes and tools. The human element is the heart and soul of the blue team and cannot be replaced by any technology or administrative procedure.
The process of selecting people is one of the most important steps in building a team. Individuals must be:
- Capable of working under pressure.
- Possessing high intelligence and strong communication skills.
- Having a continuous development mindset.
Here, quality surpasses quantity — having one person with drive and knowledge can make a huge difference to the team.
The "T-Shaped" Analyst
The ideal analyst is known as the “T-Shaped Person”, as mentioned in the book Ten Strategies of a World-Class Cybersecurity Operations Center. [Image of T-Shaped Professional Diagram]
This is the individual who:
- Possesses broad general knowledge in the field of information technology.
- Has the ability to specialize and delve deep into a specific technical area, such as digital forensics.
- Can write code, read and analyze software, and prepare detailed analytical reports.
- Has a positive energy that motivates the rest of the team.
CyberMentor Educational Platform:
Stemming from the importance of the human element, we at the CyberMentor Educational Platform work to train and qualify competencies through specialized professional bootcamps. Our goal is to build a strong base of Arab analysts and specialists capable of professionally leading SOC operations centers.
2. Process: The Roadmap for Every Team Member
Processes within the SOC center define the daily tasks for every team member: What to do? How? and When?
Processes cover everything related to incident response, forensic analysis, alert handling, threat management, and documentation.
In large organizations, specific roles like Threat Intelligence gathering can be assigned to specialists. However, in smaller organizations, individuals must be flexible and prepared to switch "hats" as needed.
The Role of Management:
SOC managers act as a "Two-Way Firewall":
- Prevent distracting the team with random requests from senior management.
- Communicate successes and critical issues to leadership in a concise and effective manner.
- Help set goals and ensure the team remains focused on priority tasks.
3. Technology: The Enabler, Not the Substitute
Technology in the SOC center is not considered a substitute for the human analyst, but rather a tool that enables and improves their performance.
The primary function of the analyst is analysis, critical thinking, and decision-making — tasks that tools cannot perform.
SOC Team Organization: Roles, Tiers, and Responsibilities
SOC teams are usually organized within a hierarchical structure that includes three main tiers:
Tier 1: Alert Triage
Dedicated to beginners, this tier involves alert triage, collecting initial data, and providing initial reports. Access tools are limited at this level.
Tier 2 and Tier 3: Advanced Analysis
As analysts gain experience, they are promoted to higher levels where they can handle more complex analytical tasks, such as:
- Forensic memory analysis.
- Malware reverse engineering.
- Direct engagement with advanced threats.
Understanding Tools and the Operating Environment
One of the most significant challenges is understanding the relationship between different tools. Therefore, we always start by explaining each system simply and abstractly.
Example: Intrusion Detection System (IDS)
- Input: Network traffic data.
- Processing: Comparison against known patterns and signatures.
- Output: Alerts displayed to the security team.
In Conclusion:
Building a successful Cybersecurity Operations Center (SOC) depends on the true integration of trained people, clear processes, and effective tools.
If you aspire to build or lead a professional SOC team, start with the foundation: build the team, organize the processes, and choose the tools carefully.
From Our Articles
What do you know about the Transmission Control Protocol (TCP)?
Have you ever wondered about the journey your email takes across the internet to reach your friends on the other side of the world with incredible speed and perfect accuracy, overcoming all aerial barriers and long distances?!
Cybersecurity job roles – The Blue Team
The Blue Team, or commonly known globally by the term 'Blue Team', is the first line of defense against cyberattacks. It is a group of individuals responsible for protecting software, systems, and networks from cyber breaches and attacks.
Cybersecurity Hardening: The Proactive Approach to System Protection
In an increasingly complex digital world, cybersecurity has become a more essential need than ever before. In previous years, most companies considered cybersecurity a luxury...
